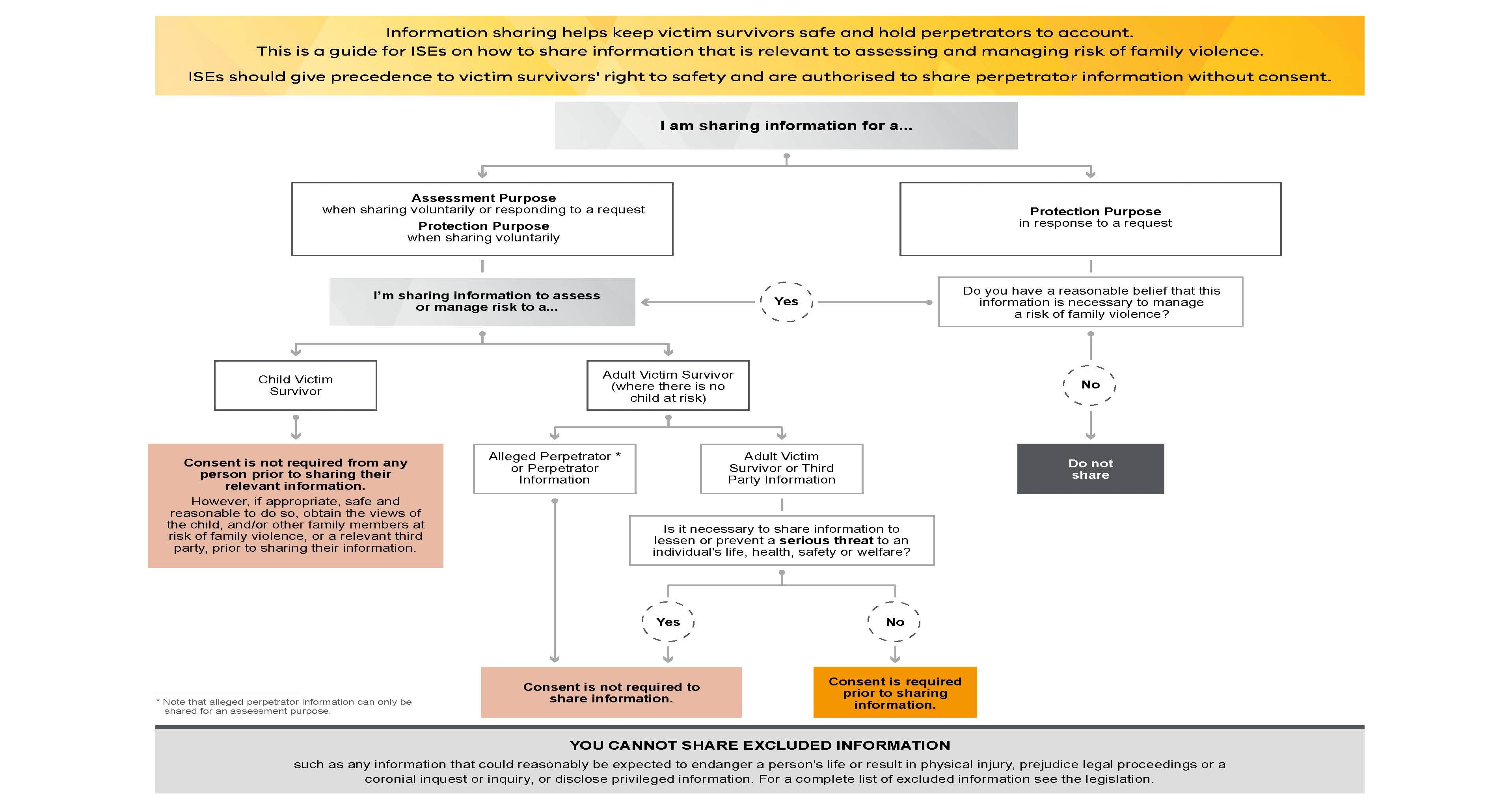
This diagram shows a process flow for sharing information about adult and child victim survivors, perpetrators, alleged perpetrators and third parties.
The diagram has an introduction text at the top, which states “Information sharing helps keep victim survivors safe and hold perpetrators to account. This is a guide for ISEs on how to share information that is relevant to assessing and managing risk of family violence. ISEs should give precedence to victim survivors' right to safety and are authorised to share perpetrator information without consent.”
The top level (first level) starts with “I am sharing information for a...”. Option 1 is both “Assessment Purpose (when sharing voluntarily or responding to a request) and Protection Purpose (when sharing voluntarily)”, and option 2 is “Protection Purpose (in response to a request)“.
If option 1 to this first level Q, then Q: “I’m sharing information to assess or manage risk to a...”. Options for this second level Q are: “Child Victim Survivor” and “Adult Victim Survivor (where there is not child at risk)”.
If “Child Victim Survivor”, then process flow ends with “Consent is not required from any person prior to sharing their relevant information. However, if appropriate, safe and reasonable to do so, obtain the views of the child, and/or other family members at risk of family violence, or a relevant third party, prior to sharing their information.”
If “Adult Victim Survivor (where there is not child at risk)”, then options are “Alleged Perpetrator (note that alleged perpetrator information can only be shared for an assessment purpose) or Perpetrator Information” and “Adult Victim Survivor or Third Party Information”. If “Alleged Perpetrator or Perpetrator Information”, then process flow ends with “Consent is not required to share information.”
If “Adult Victim Survivor or Third Party Information”, then Q: “Is it necessary to share information to lessen or prevent a serious threat to an individual's life, health, safety or welfare?”. If yes, then process flow ends with “Consent is not required to share information.” If no, then process flow ends with “Consent is required prior to sharing information.”
If option 2 to the first level Q, then Q: “Do you have a reasonable belief that this information is necessary to manage a risk of family violence?”. If yes, then process flow goes to the second level Q: “I’m sharing information to assess or manage risk to a...” (see above paragraphs for the flow for this. If no, then process flow ends with “Do not share”.
The diagram has the following text in the footer: “You cannot share excluded information", such as any information that could reasonably be expected to endanger a person's life or result in physical injury, prejudice legal proceedings or a coronial inquest or inquiry, or disclose privileged information. For a complete list of excluded information see the legislation.”
Updated